In this post I will show you how to setup Active Directory Authentication in vSphere 4.1.
What do we need tot do:
– Before you start. Please make sure that DNS and NTP are fully functional.
– Create an AD group called "ESX Admins" on a Windows Domain Controller
– Add users to that group
– Configure ESX/ESXi server’s "Directory Services"
If your ESX hosts and Active Directory Domain controllers are able to find each other via DNS, you’re ready to go to the next step of this setup. We need to create a group called “ESX Admins” and add the users with administrator permissions in vCenter to this group. When you choose a different name for the group, you will not be able to use Active Directory Authentication. I found this in the vsp_41_esx_server_config.pdf:
vCenter Server registers any selected Windows domain user or group through the process of assigning permissions. By default, all users who are members of the local Windows Administrators group on vCenter Server are granted the same access rights as any user assigned to the Administrator role. Users who are members of the Administrators group can log in as individuals and have full access.
Users who are in the Active Directory group ESX Admins are automatically assigned the Administrator role.
After creating the ESX Admins group it’s now time to join the ESX host to the Windows Domain. When you’re managing a small environment, you can do this with five a six mouse clicks per ESX host.
Log on to vCenter en select a host from the Hosts and Clusters view. Click on the Configuration tab en select Authentication Services. You can change the setting via Properties:
Now select Active Directory in the Select Directory Service Type. Enter the Domain details and click on Join Domain:
Enter the Administrator credentials and click again on Join domain:
The ESX host is now joined to the domain. You can verify this by opening Active Directory Users and Computers. Now you will see the ESX hosts under the Computers folder.
The configuration steps are finished. Now you’re able to use Active Directory authentication to logon directly via the vSphere client on an ESX host in your Cluster.
Or you can logon through SSH via your Active Directory credentials:
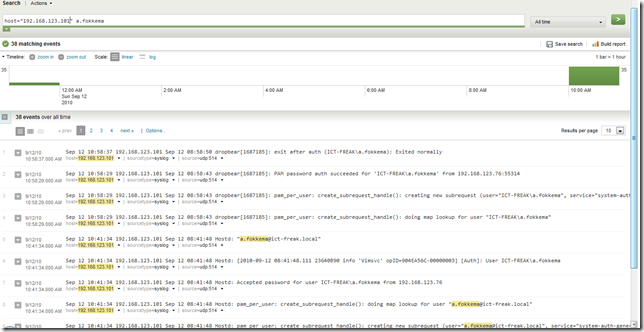
You can see the logon process in you logs. In my case you see Splunk:
Instead of configuring all the host via the five a six mouse clicks. You can also use LucD22 his PowerCLI Set-VMHostADDomain function. You can find this function here: http://www.lucd.info/2010/07/25/script-vsphere-4-1-ad-authentication/ The best way to use this function is to add it to your Powershell Profile (more info about this subject can be found here: http://msdn.microsoft.com/en-us/library/bb613488(VS.85).aspx). When you added this function to your profile, you’re able to configure all your ESX hosts to authenticate via Active Directory, You can do this by running the following PowerCLI one-liner:
Get-VMHost | Set-VMHostADDomain -ADJoin:$true -Domain ‘ict-freak.local’ -Credential (Get-Credential)
To get an overview of all the ESX hosts and their configuration. You can run the following PowerCLI one-liner. You also need LucD22 his function mentioned above to run this one-liner:
get-vmhost | % {Get-VMHostAuthentication $_} | ft
The following output will be generated:
Sources:
| Source: | Link: |
| VMware | http://www.vmware.com/pdf/vsphere4/r41/vsp_41_esx_server_config.pdf page: 176 |
| Trainsignal | http://www.vmwarevideos.com/video-new-vsphere-4-1-windows-active-directory-authentication |
| LucD | http://www.lucd.info/2010/07/25/script-vsphere-4-1-ad-authentication/ |
| VMware KB | KB1021970 |







What if the AD server insists on SSL?
What about adding the host to AD from the service console? I can’t find any documentation on this anywhere.
Thanks for this, it would be good to change the hardcoded ESX Admins group
I’m not sure the ESX Admins group is a requirement as such. I was able to assign the Domain Admins group to an ESXi host and after AD synched (about 15 minutes or so) I could authenticate with the vSphere client directly to this ESXi host.
This is ESXi, so no direct SSH. Still working on the vMA and AD…
Nice guide. When you ssh to the server, were you able to su to root or sudo any root commands? I was able to configure the AD authentication piece, but I can’t for the life of me figure out how to give my AD account su or sudo privileges!
Thanks,
-Loren
Yes, you’re able to perform su – on the ssh console.This works out of the box on a Classic (ESX) vSphere host
I tried the below command in vSphere 4.0 environment and it threw an error. Is it specific to 4.1?
[vSphere PowerCLI] C:\> get-vmhost | % {Get-VMHostAuthentication $_} | ft
The term ‘Get-VMHostAuthentication’ is not recognized as the name of a cmdlet, function, script f
ile, or operable program. Check the spelling of the name, or if a path was included, verify that
the path is correct and try again.
At line:1 char:41
+ get-vmhost | % {Get-VMHostAuthentication <<<< $_} | ft
+ CategoryInfo : ObjectNotFound: (Get-VMHostAuthentication:String) [], CommandNotFo
undException
+ FullyQualifiedErrorId : CommandNotFoundException
AD integration is a feature which is introduced in vSphere 4.1.
don’t forget to go to Permissions tab and add the AD group to be able to login to the client.